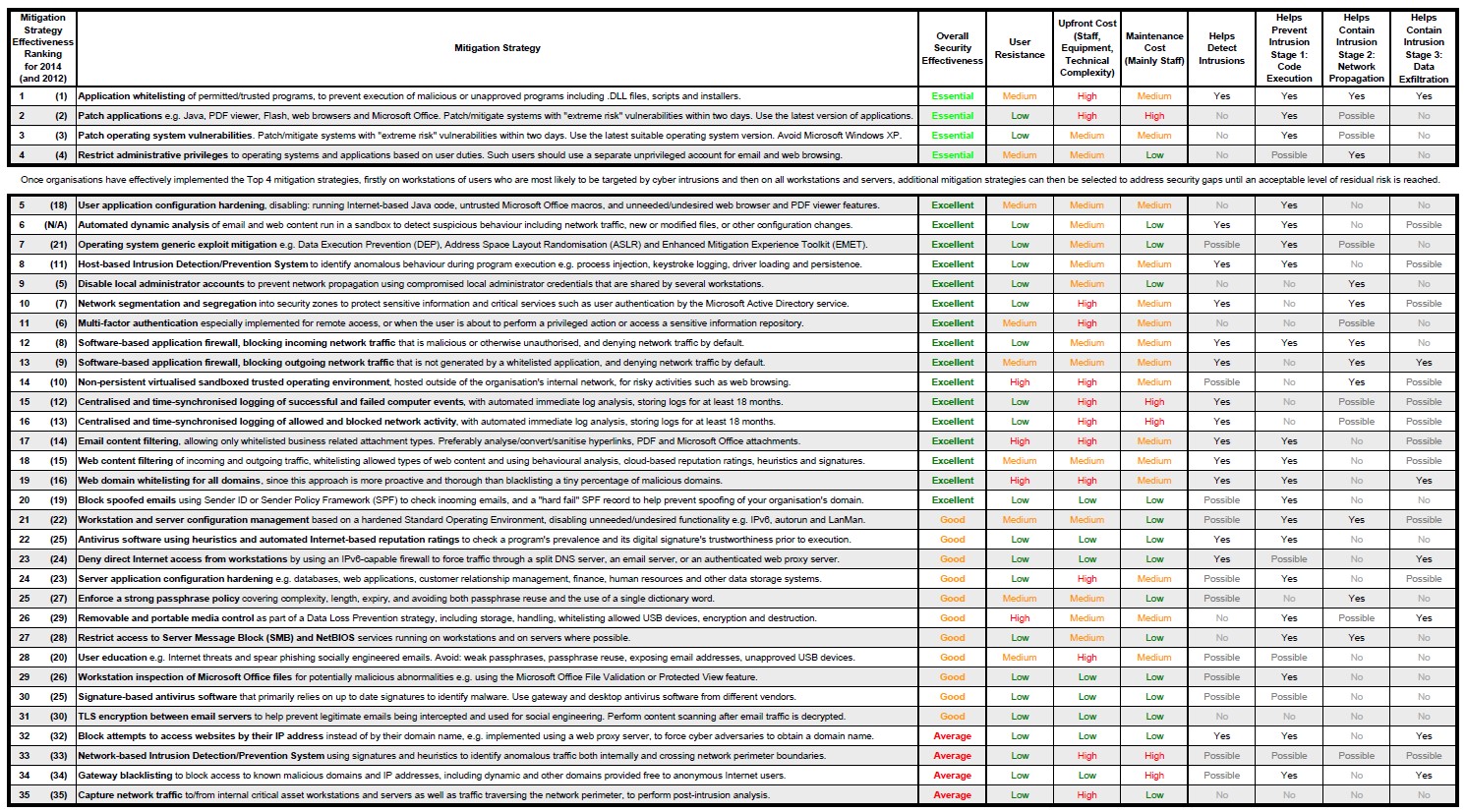
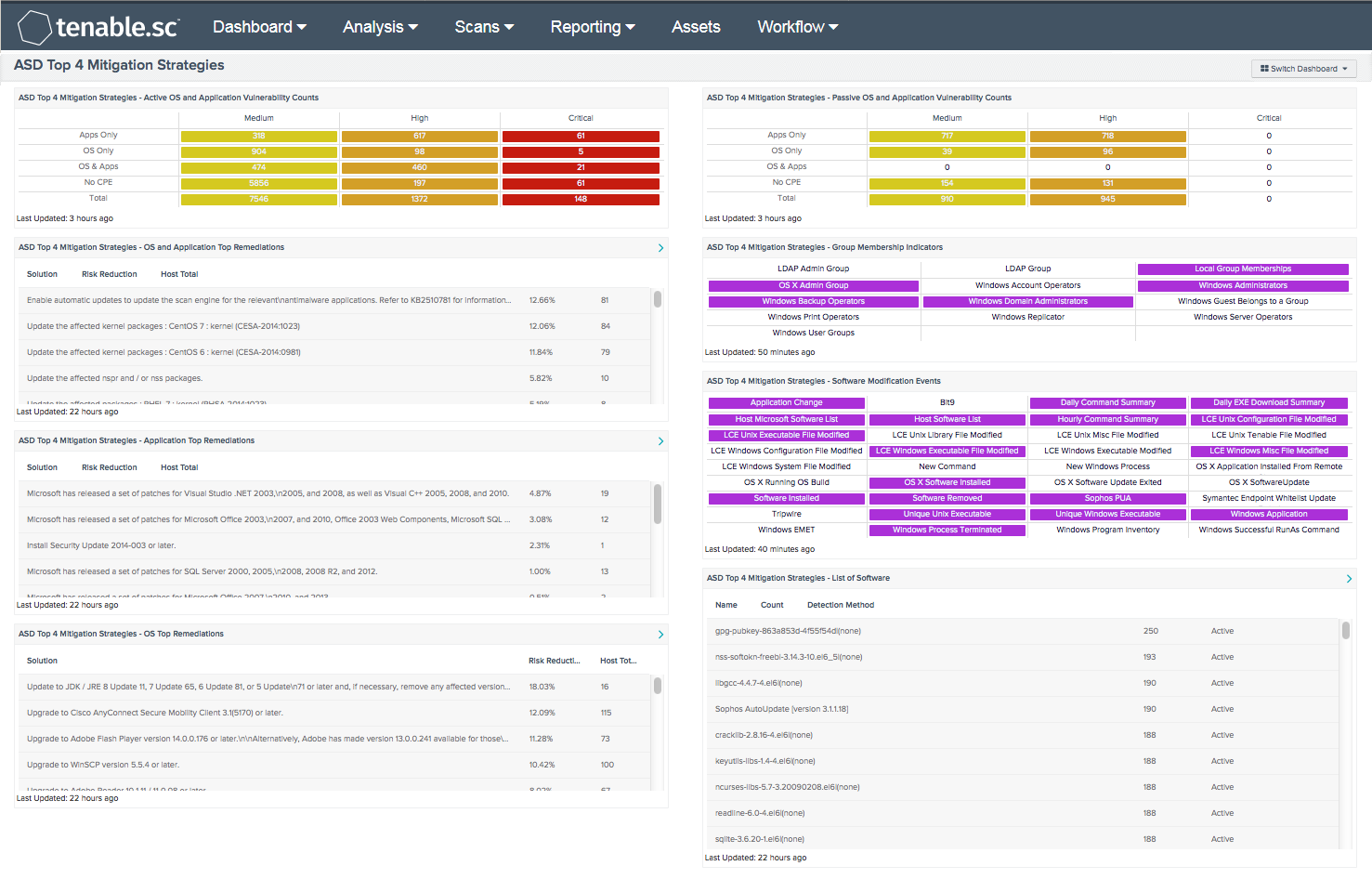
Chapter 12 Operating System Security Strategies The 2010 Australian Signals Directorate (ASD) lists the “Top 35 Mitigation Strategies” Over 85% of. - ppt download
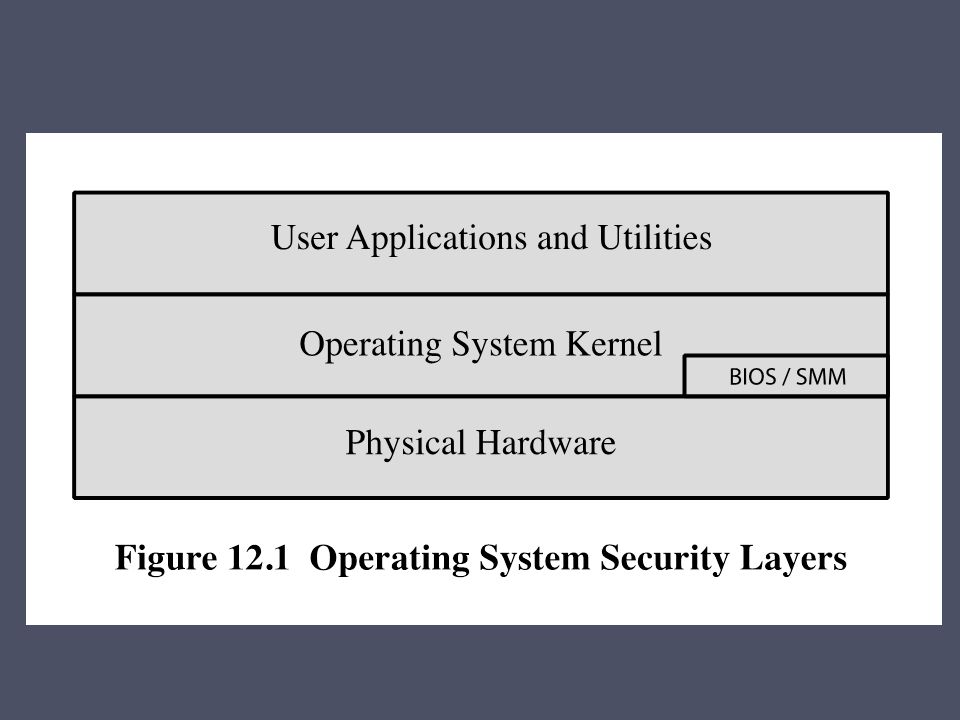
Chapter 12 Operating System Security Strategies The 2010 Australian Signals Directorate (ASD) lists the “Top 35 Mitigation Strategies” Over 85% of. - ppt download

Situational Crime Prevention and the Mitigation of Cloud Computing Threats Chaz Vidal Supervisor: Raymond Choo. - ppt video online download
34 LONG condition between TD and ASD. Top figure illustrates the t/f... | Download Scientific Diagram
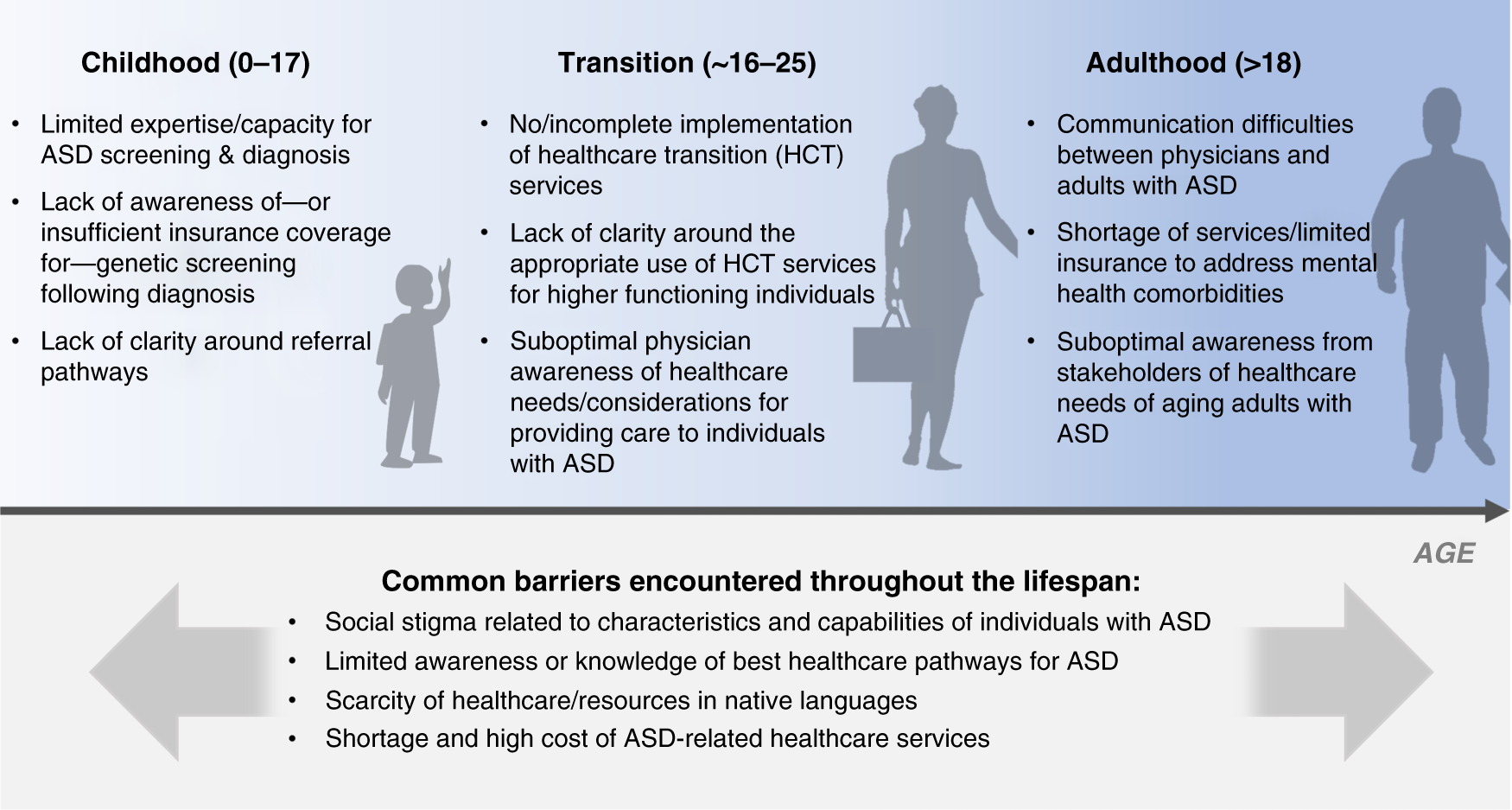
Tackling healthcare access barriers for individuals with autism from diagnosis to adulthood | Pediatric Research

Important features for classification are different across sub-groups.... | Download Scientific Diagram
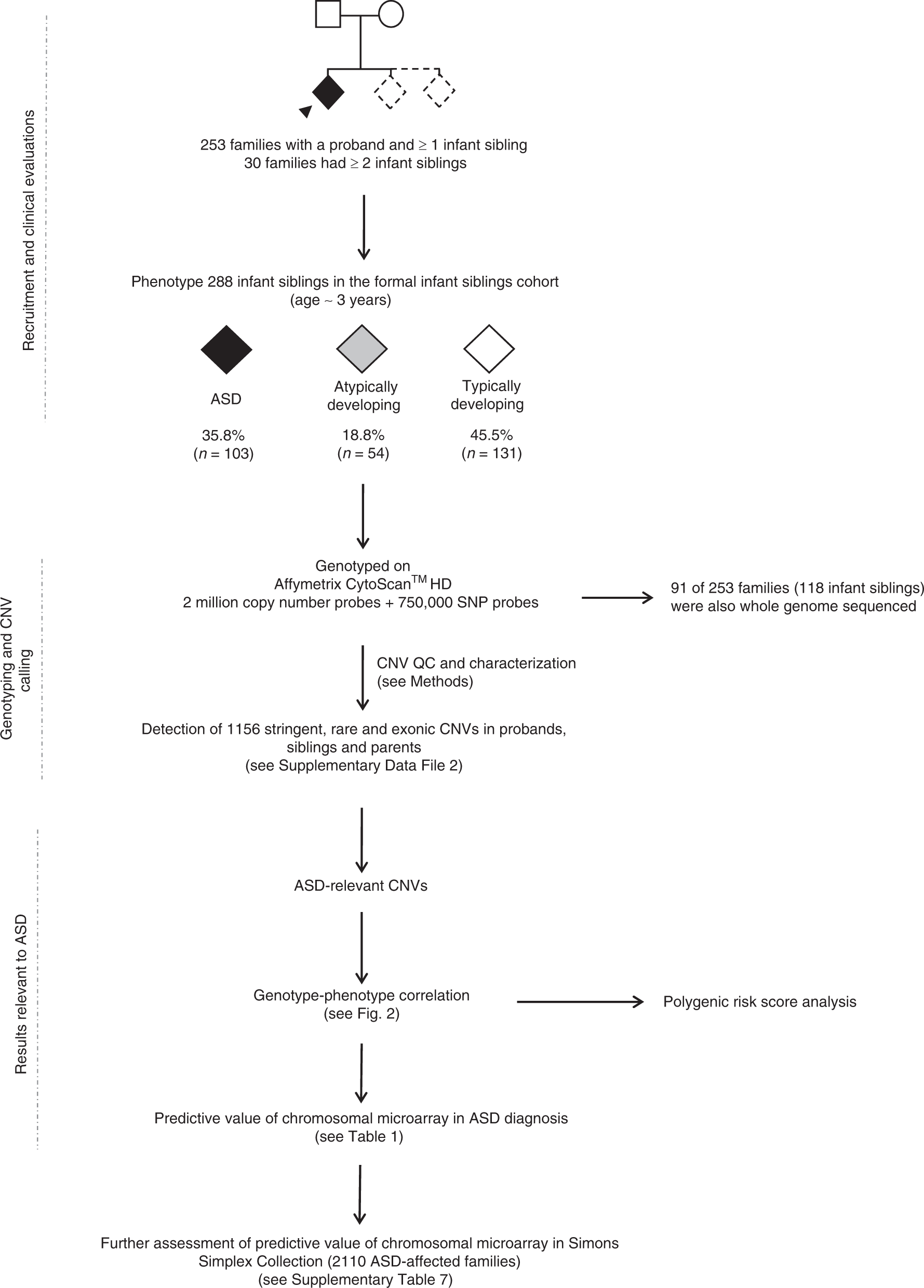
Predictive impact of rare genomic copy number variations in siblings of individuals with autism spectrum disorders | Nature Communications

Buy ASD 2x4Ft LED Edge Lit Panel Light Color Temperature Selectable 3000-5000K, Power Adjustable 35-50W with Motion Sensor - 5250 Lm, 120-277V Indoor Commercial Fixture, UL & DLC, 2 Pack Online in Poland. B08VDNSFC7

Chapter 12 Operating System Security Strategies The 2010 Australian Signals Directorate (ASD) lists the “Top 35 Mitigation Strategies” Over 85% of. - ppt download
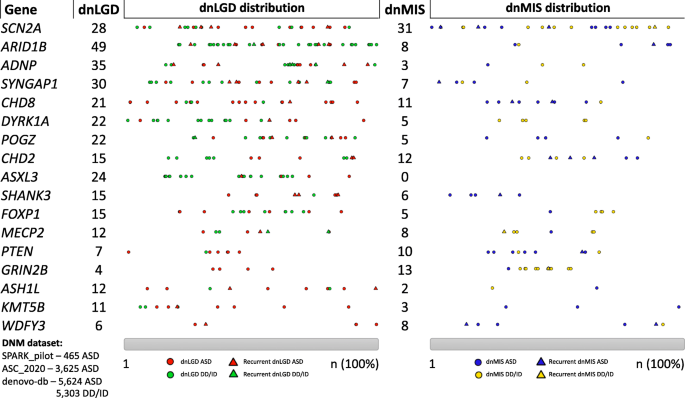
Reflections on the genetics-first approach to advancements in molecular genetic and neurobiological research on neurodevelopmental disorders | Journal of Neurodevelopmental Disorders | Full Text